|
|
The Good
This week, the UK’s NCSC (National Cyber Security Centre) released its 2021 Annual Review, which covers the agency’s cyber-related insights and facts from September 2020 to August 2021. Some of the highlights include the agency taking down 2.3 million cyber-enabled commodity campaigns, including over 400 phishing campaigns, and the removal of more than 50,000 scam emails and over 90,000 malicious URLs.

On the downside, the agency reported that 39% of all UK businesses (around 2.3 million) reported a cyber breach or attack in 2020/2021. The agency also reports that one of the core threats faced this year came from zero-day vulnerabilities in Microsoft Exchange Servers, which are estimated to have led to at least 30,000 organizations being compromised in the U.S. alone.
Ransomware, predictably, was named the top threat facing businesses, with the agency declaring that in the first four months of 2021, it dealt with the same number of ransomware incidents as in the whole of 2020, a figure that itself was three times greater than in 2019. Top vectors for ransomware infections seen by the NCSC were insecure RDP (remote desktop protocol), vulnerabilities in VPNs (Virtual Private Networks) and a variety of known but unpatched software vulnerabilities.
Nonetheless, the NCSC report contains a lot of practical advice for organizations looking to improve cyber resilience in the face of these increasing threats, and security teams are encouraged to review the NCSC’s report and guidelines.
The Bad
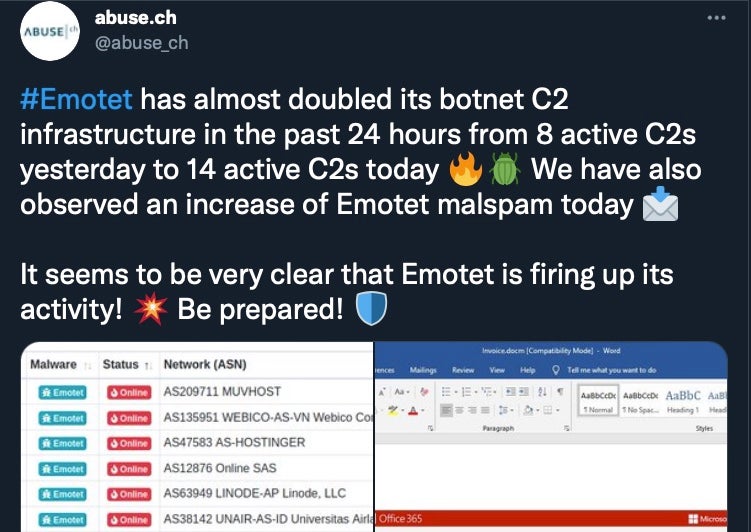
Like a bad penny, Emotet keeps on popping up just when you thought you had seen the last of it. In recent weeks, rival malspam loader SquirrelWaffle has been receiving a lot of attention in the 10-month absence of any Emotet activity. Perhaps not to be outdone by this “new kid on the block”, fresh Emotet malspam laced with poisoned Word and Excel document attachments were spotted this week.
The malicious documents make use of macros to launch a PowerShell command that retrieves the Emotet loader DLL from a remote URL and saves it to the ProgramData folder on the C: drive. Rundll32.exe is then used to copy the DLL to a randomly named folder in %LocalAppData% and then relaunch it from that location. After setting a Registry key for persistence, the malware runs in the background awaiting commands from a C2.
The return of Emotet after its very high-profile takedown back in January, when traffic across all tiers of the Emotet infrastructure had been seized and redirected to systems controlled by law enforcement, will be of concern to all IT and security teams. First observed being dropped last Sunday by TrickBot infections, researchers say that Emotet malware is rebuilding its botnet and already has over 200 infected devices acting as C2s.
Good endpoint security measures are vital to detecting and protecting against Emotet. Admins are also advised to keep up to date with the latest Emotet URLs here.
The Ugly
Despite the ramping up of ransomware interventions by the U.S. government in recent weeks, there are good reasons why ransomware isn’t going away anytime soon, chief among those being the exploitation of vulnerabilities in certain enterprise products. Exploitable bugs in Microsoft and Fortinet software are in focus once again this week as a joint advisory warns Iranian hackers are using these to target critical infrastructure with ransomware.
The advisory notes that Iranian government-sponsored APT actors are targeting a wide range of critical infrastructure sectors, including Transportation and Healthcare. CISA and the FBI have observed these actors exploit the Microsoft Exchange ProxyShell vulnerability as well as Fortinet vulnerabilities in an effort to gain initial access for follow-on operations including the deployment of ransomware.

Specifically, CISA warn that these actors have been leveraging CVE-2021-34473 (aka ProxyShell) against both U.S. and Australian organizations. Once access was gained, the APT actors used BitLocker activation to encrypt data on host networks and drop ransom notes with the following contact addresses:
- sar_addr@protonmail[.]com
- WeAreHere@secmail[.]pro
- nosterrmann@mail[.]com
- nosterrmann@protonmail[.]com
Other indicators of compromise include the following IP addresses:
- 91.214.124[.]143
- 162.55.137[.]20
- 154.16.192[.]70
Further IoCs including file hashes and MITRE TTPs are available on the CISA advisory page.
This activity is a timely reminder to organizations that if you don’t patch vulnerabilities, threat actors will find you out. Similarly, if you use enterprise software without proven behavioral AI security controls, don’t be surprised if threat actors go unnoticed while punching a whole through that firewall or operating system software.