|
|
SentinelOne is pleased to announce early availability (EA) of the integration between our real-time, AI-powered Cloud Workload Protection Platform (CWPP) with the Wiz Cloud-Native Application Protection Platform (CNAPP) functionality. This “shift-left, shield right” combination of Wiz and SentinelOne in a multi-layered cloud security stack helps cloud security practitioners quickly and easily identify, prioritize, and fix cloud security incidents more efficiently.
When SentinelOne detects a runtime threat to a cloud server or container, it automatically ingests relevant context from Wiz about that cloud resource, including any vulnerabilities, misconfigurations, and exposed secrets that Wiz has detected on it. The SentinelOne threat is automatically enriched with this information in the SentinelOne Singularity™ Platform console. This helps cloud security teams improve security outcomes, including faster and more effective triage, prioritization, and time to remediation. Through the integration of Wiz and SentinelOne products, security teams can now:
- Visualize their cloud security posture in real time
- Identify attack paths to critical cloud resources
- Prioritize cloud risks and quickly triage them to reduce risk
- Protect cloud workloads from build time to runtime
- Speed mean time to detection and remediation of cloud incidents

Getting Started
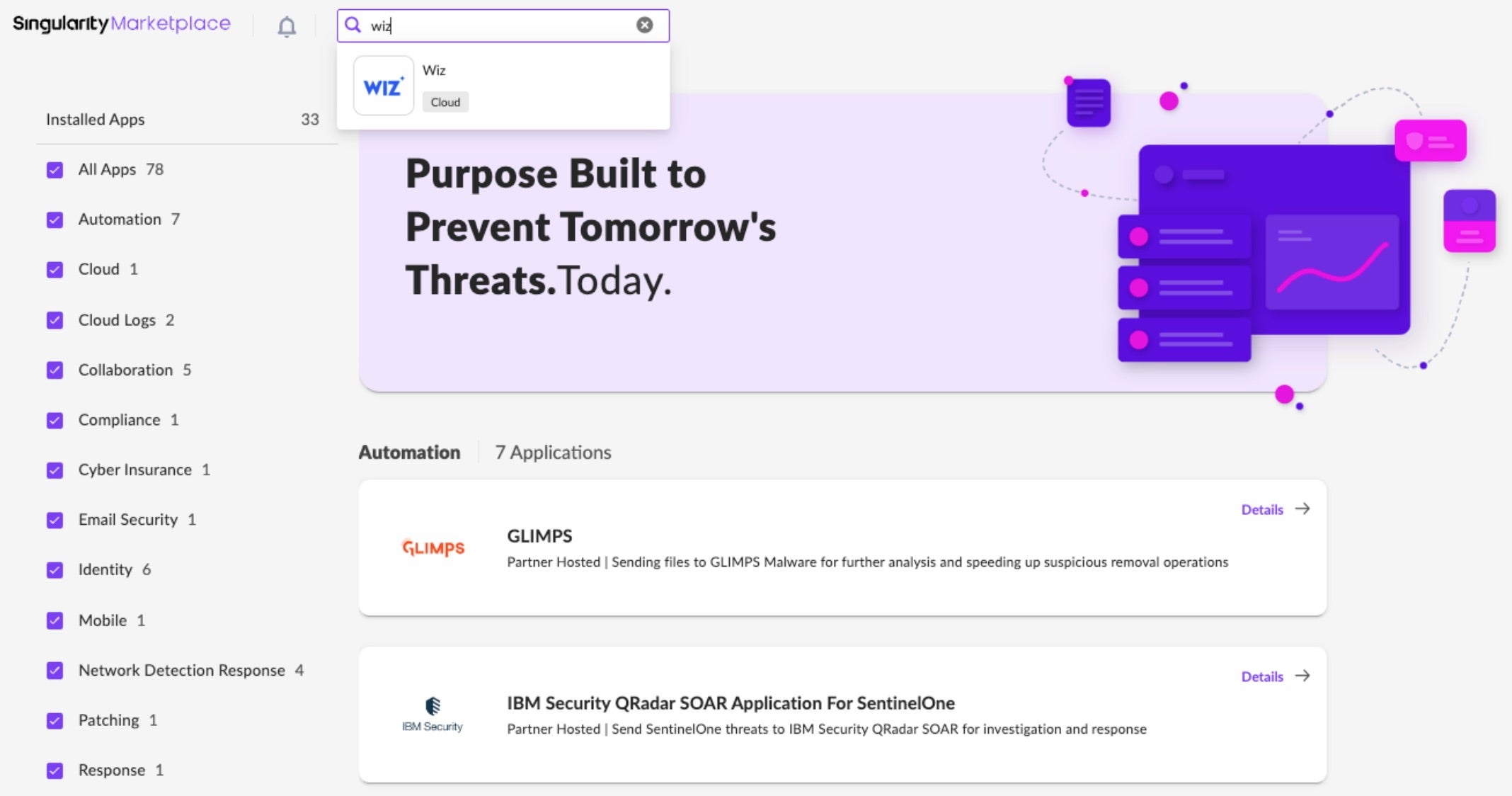
To get started, SentinelOne customers can navigate to the Singularity Marketplace from within the management console and search for Wiz. Select the Wiz app and install (See Figure 1).
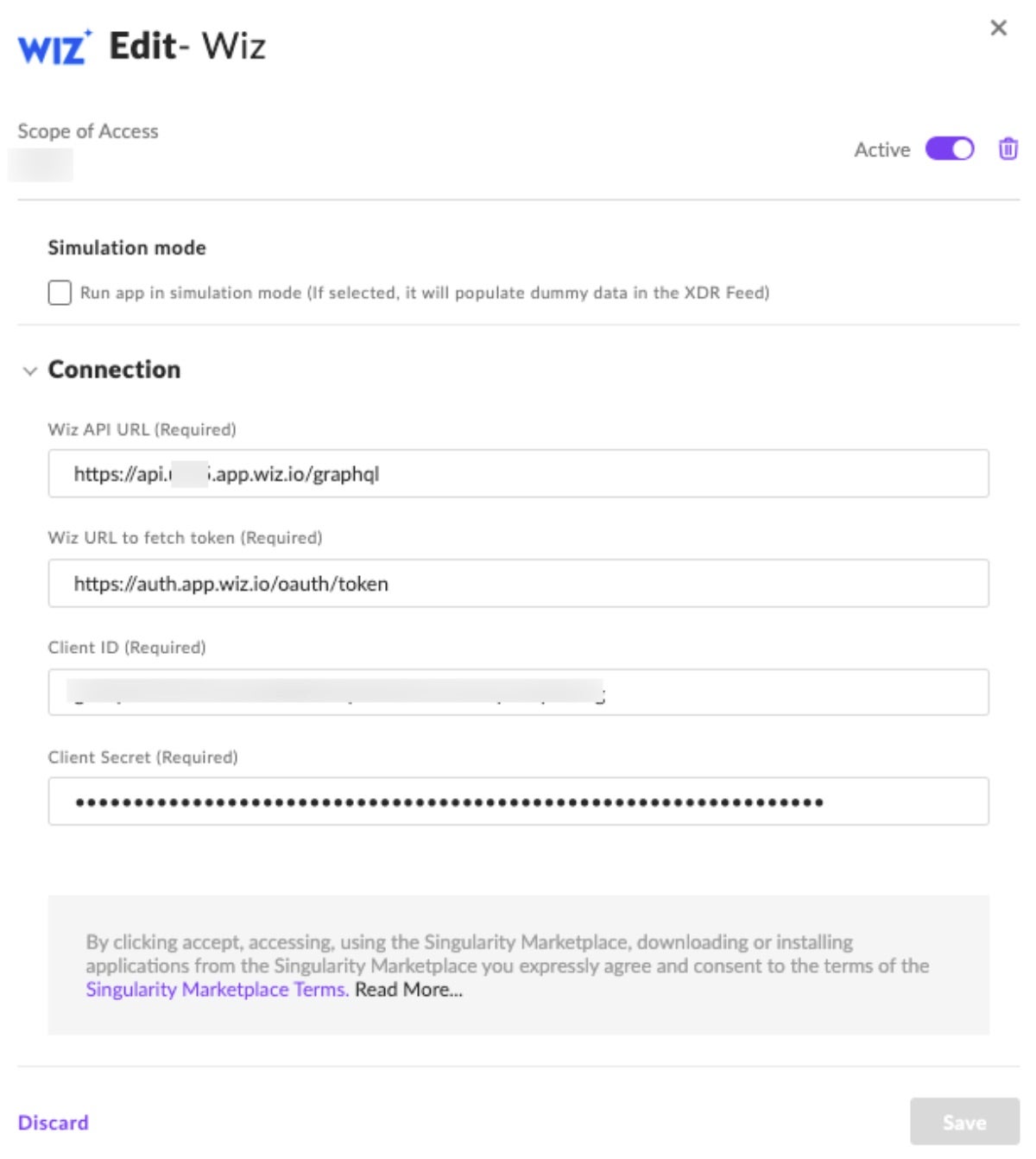
To configure the integration (see Figure 2), the “Wiz API URL” value can be found from the Wiz console via:
- Clicking on the user icon in the top right corner and selecting “User Settings”.
- In the left hand menu, select “Tenant”.
- Copy the value for “API Endpoint URL” and paste it into the “Wiz API URL” field of the Singularity Marketplace app for Wiz.
The value for “Wiz URL to fetch token” will be https://auth.app.wiz.io/oauth/token. And the values for “Client ID” and “Client Secret” can be obtained by creating a new Service Account in the Wiz console. For instructions, please refer to the Wiz documentation on the topic. Then, simply save the configuration and your integration between the Wiz and SentinelOne platforms is ready to use.
From any Threat Details screen within the SentinelOne management console, click the XDR tab to review related context from Wiz – called “Issues” – for the underlying cloud resource (e.g., Amazon EC2 instance).
Threat Detection, Enriched
Singularity Cloud Workload Security is SentinelOne’s real-time CWPP solution for workloads, on-prem or in the cloud, on VMs, containers, or Kubernetes clusters. It stops runtime threats such as ransomware, zero-day exploits, and memory injections from disrupting cloud operations or compromising company secrets. Machine-speed threats such as these require the machine-speed detection and response that only a real-time solution can provide. Working alongside a “shift-left” solution such as Wiz – which scans for software vulnerabilities, excessive permissions, misconfigurations, and more – only makes the cloud security stack that much more compelling.
Upon detecting a runtime threat, Singularity Cloud Workload Security automatically ingests issue details from Wiz, enriching threat details with context on the underlying infrastructure. For example, a suspicious threat detected on an Amazon EC2 instance (see Figure 3) is enriched with details such as whether the instance is exposed to the internet, has excessive permissions, and/or contains a vulnerability with a known exploit.
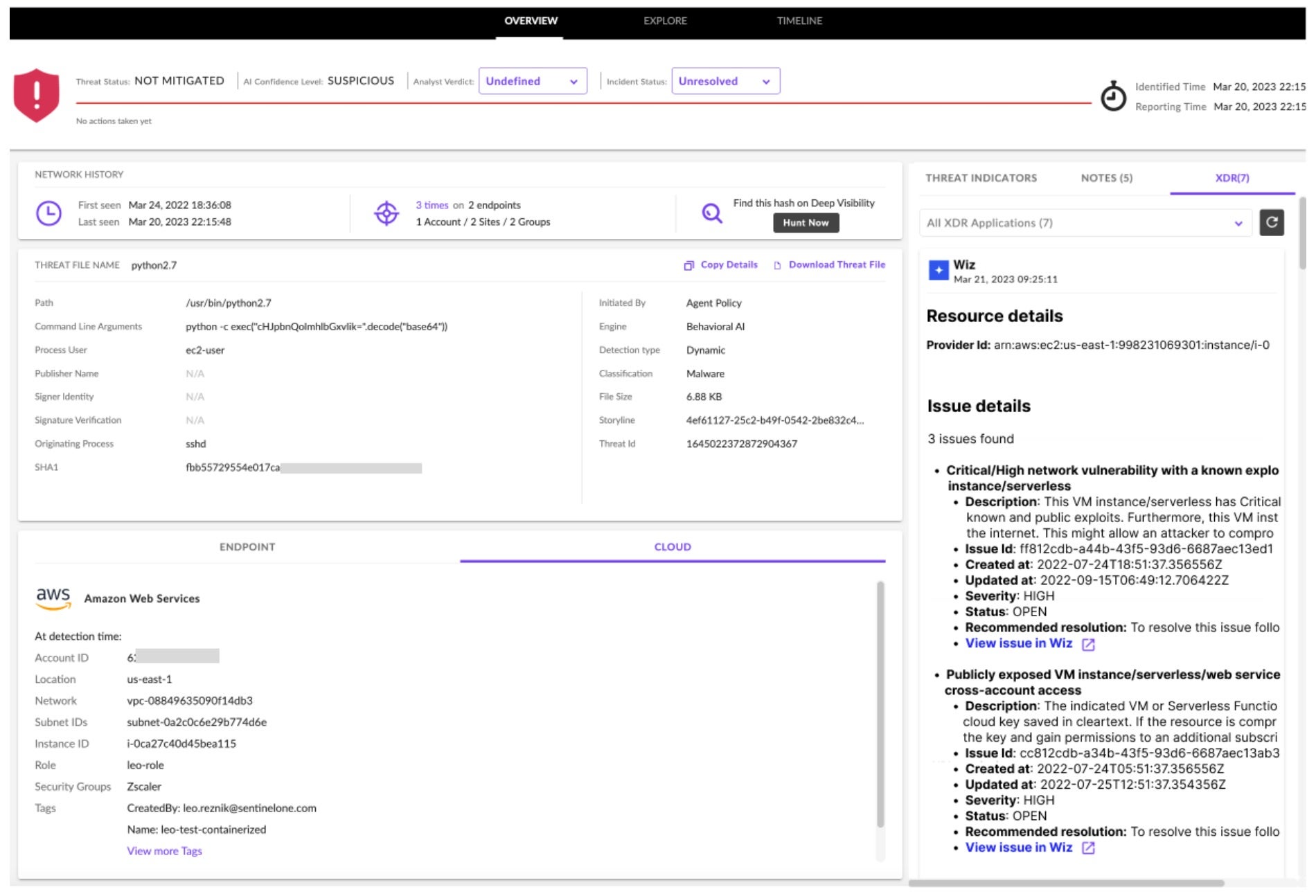
Wiz had previously scanned the infrastructure, identifying that this specific cloud compute instance is publicly exposed to the internet, via a cloud access key that was saved in cleartext on a public repository such as GitHub. Moreover, this instance has a critical or high network vulnerability with a known exploit. These supporting details are extraordinarily helpful to the security practitioner during triage. Not only is the investigation streamlined, the incident can be routed to the appropriate DevOps owner with all haste.
Additionally, a deep link from the cloud resource issues attached to the threat details can take the user – whether a security practitioner, or the DevOps owner – from the SentinelOne console directly into the Wiz console. As a matter of convenience and efficiency, the user can then examine the attack path in Wiz Security Graph, run queries to identify what other instances may have the same vulnerabilities, and take corrective action such as updating the workload image to prevent recurrence. Meanwhile, back in the SentinelOne console, the security user can remediate the incident, either with a single click or in a fully-automated, machine-speed fashion governed by policy which the security admin controls.
Summary
By enriching cloud runtime threats detected by Singularity Cloud Workload Security with context from Wiz on the underlying cloud resources directly within the SentinelOne console, security practitioners can better protect cloud workloads from build time to runtime. Through better prioritization, streamlined investigation, and simplified remediation, security can better manage risk and slash mean-time-to-repair. Each solution works alongside the other to set the stage for improved cloud operations, innovation, and ROI.
To learn more, visit us at RSAC 2023 at booth S-626, where we are demonstrating this exciting integration. Won’t be at RSAC this year? Not a problem. Navigate over to our solution homepage to learn more and, when you are ready, connect with one of our cloud security experts for a demo.



