Executive Summary
- SentinelLabs has identified a new cluster of threat activity targeting Russian organizations.
- We assess with high-confidence that the threat actor responsible for the attacks is a Chinese state-sponsored cyber espionage group, as also recently noted by Ukraine CERT (CERT-UA).
- The attacks use phishing emails to deliver Office documents to exploit targets in order to deliver their RAT of choice, most commonly Bisonal.
- SentinelLabs has also identified associated activity targeting telecommunication organizations in Pakistan leveraging similar attack techniques.
Overview
On June 22nd 2022, CERT-UA publicly released Alert #4860, which contains a collection of documents built with the Royal Road malicious document builder, themed around Russian government interests. SentinelLabs has conducted further analysis of CERT-UA’s findings and has identified supplemental Chinese threat activity.
China’s recent intelligence objectives against Russia can be observed in multiple campaigns following the invasion of Ukraine, such as Scarab, Mustang Panda, ‘Space Pirates’, and now the findings here. Our analysis indicates this is a separate Chinese campaign, but specific actor attribution is unclear at this time.
While the overlap of publicly reported actor names inevitably muddies the picture, it remains clear that the Chinese intelligence apparatus is targeting a wide range of Russian-linked organizations. Our findings currently offer only an incomplete picture of this threat cluster’s phishing activity, but they serve to provide perspective into an attacker’s ongoing operational objectives and a framework for our ongoing research.
Malicious Documents Targeting Russia
On June 22nd , Ukraine’s CERT-UA reported several RTF documents containing malicious code exploiting one or more vulnerabilities in MS Office. CERT-UA assessed that the documents, “Vnimaniyu.doc”, “17.06.2022_Protokol_MRG_Podgruppa_IB.doc”, and “remarks table 20.06.2022_obraza”, were likely built with the Royal Road builder and dropped the Bisonal backdoor. Royal Road is a malicious document builder used widely by Chinese APT groups, while Bisonal is a backdoor RAT unique to Chinese threat actors.
The CERT-UA advisory followed public reporting by our colleagues from nao_sec and Malwarebytes, who identified some of the first indicators and shared related samples and C2 servers. Building off this initial intelligence, SentinelLabs discovered a further related cluster of activity.
As we have observed over the years, Royal Road documents follow content themes relevant to their targets. Following that practice, it’s reasonable to assume that the targets in this recent cluster of activity are likely Russian government organizations.
One example of this cluster (f599ed4ecb6c61ef2f2692d1a083e3bb040f95e6) is a fake document mimicking a RU-CERT memo on increased phishing attacks.
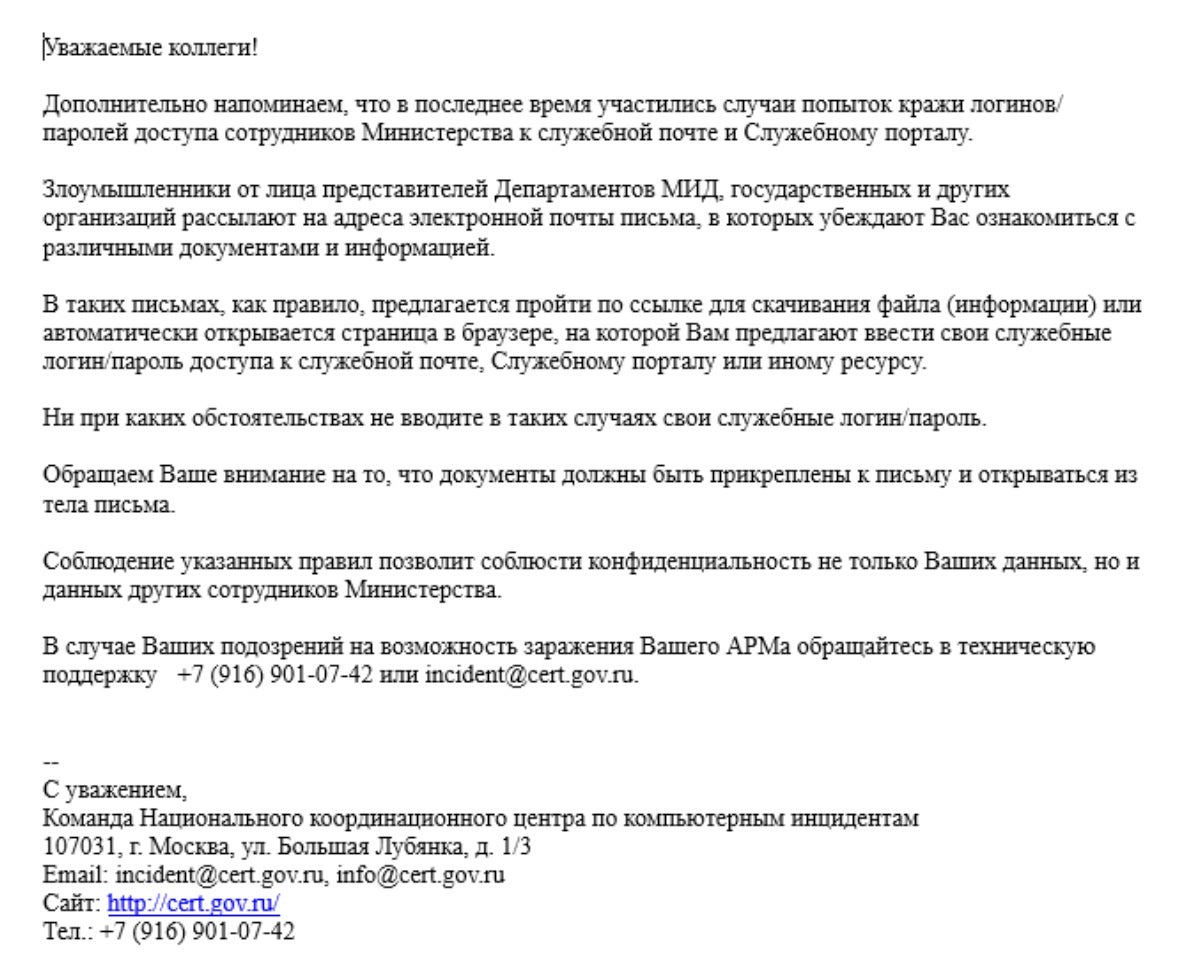
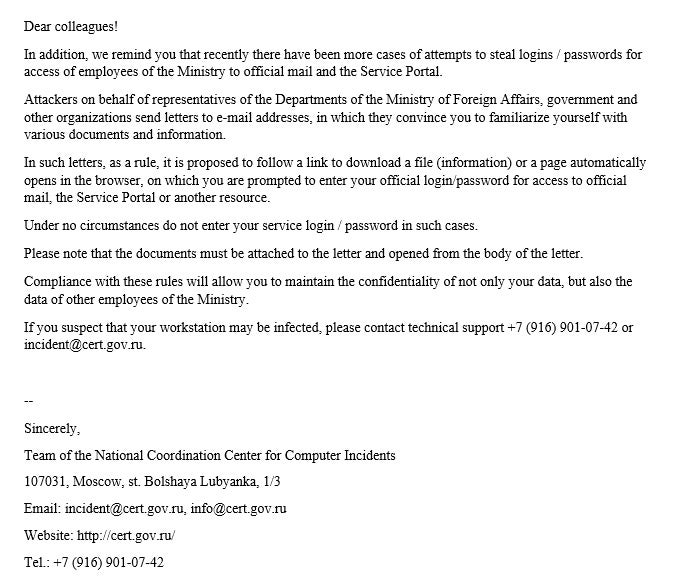
Another example is themed around telecommunication organizations (415ce2db3957294d73fa832ed844940735120bae).


The example documents shown above both exploit CVE-2018-0798, a remote execution vulnerability in Microsoft Office to install the embedded malware.
Attribution to Chinese Threat Groups
The collection of files and infrastructure noted above could be considered related to the Tonto Team APT group (aka “CactusPete”, “Earth Akhlut”), a Chinese threat group that has been reported on for nearly ten years. However, we assess that link with only medium confidence due to the potential for shared attacker resources that could muddy attribution based on the currently available data. Known targets span the globe, with a particular interest in Northeast Asia, including governments, critical infrastructure, and other private businesses.
The attacker continues their long history of Russian targeting; however, the rate of Russian and Russia-relevant targets in recent weeks may indicate increased prioritization.
There are multiple connections of this activity to Chinese threat actors. As noted above, the documents are built with a commonly known malicious document builder used widely by Chinese APT groups, the shared toolkit often referred to as the “Royal Road” or the “8.t” builder.
These documents often contain metadata indicating the document creator’s operating system was using simplified Chinese, a trait we observed in our previous analysis of Scarab APT activity.
The malicious documents are generally used for the delivery of custom malware, such as the Bisonal RAT, which as noted by CERT-UA, is unique to Chinese groups, including Tonto Team. Bisonal has a uniquely long history of use and continued development by its creators, such as expanding features for file searching and exfiltration, anti-analysis and detection techniques, and maintaining generally unrestricted system control.
Additionally, the collection of C2 infrastructure associated with these various samples fall under a larger umbrella of known Chinese APT activity.
Related Activity of Interest
It’s also worth noting that there are still ongoing related attacks focused on non-Russian organizations, such as those against Pakistan.
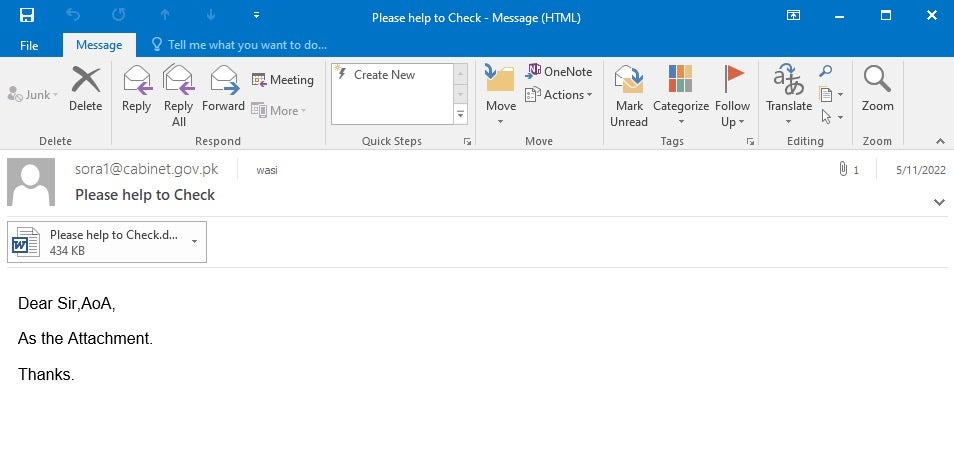
For example, one file uploaded to VirusTotal (91ca78231bcacab0d5e6194041817b96252e65bf) from Pakistan is a May 2022 email message file to the Pakistan Telecommunication Authority, sent from a potentially compromised account in the Cabinet Division of the Pakistani government. This email contains the Royal Road attachment “Please help to Check.doc” (f444ff2386cd3ada204c3224463f4be310e5554a), dropping 85fac143c52e26c22562b0aaa80ffe649640bd29 and beaconing outbound to instructor.giize[.]com (198.13.56[.]122).
Conclusion
We assess with high confidence that the Royal Road-built malicious documents, delivered malware, and associated infrastructure are attributable to Chinese threat actors. Based on our observations, there’s been a continued effort to target Russian organizations by this cluster through well-known attack methods– the use of malicious documents exploiting n-day vulnerabilities with lures specifically relevant to Russian organizations. Overall, the objectives of these attacks appear espionage-related, but the broader context remains unavailable from our standpoint of external visibility.
Indicators of Compromise
| IOC | Description |
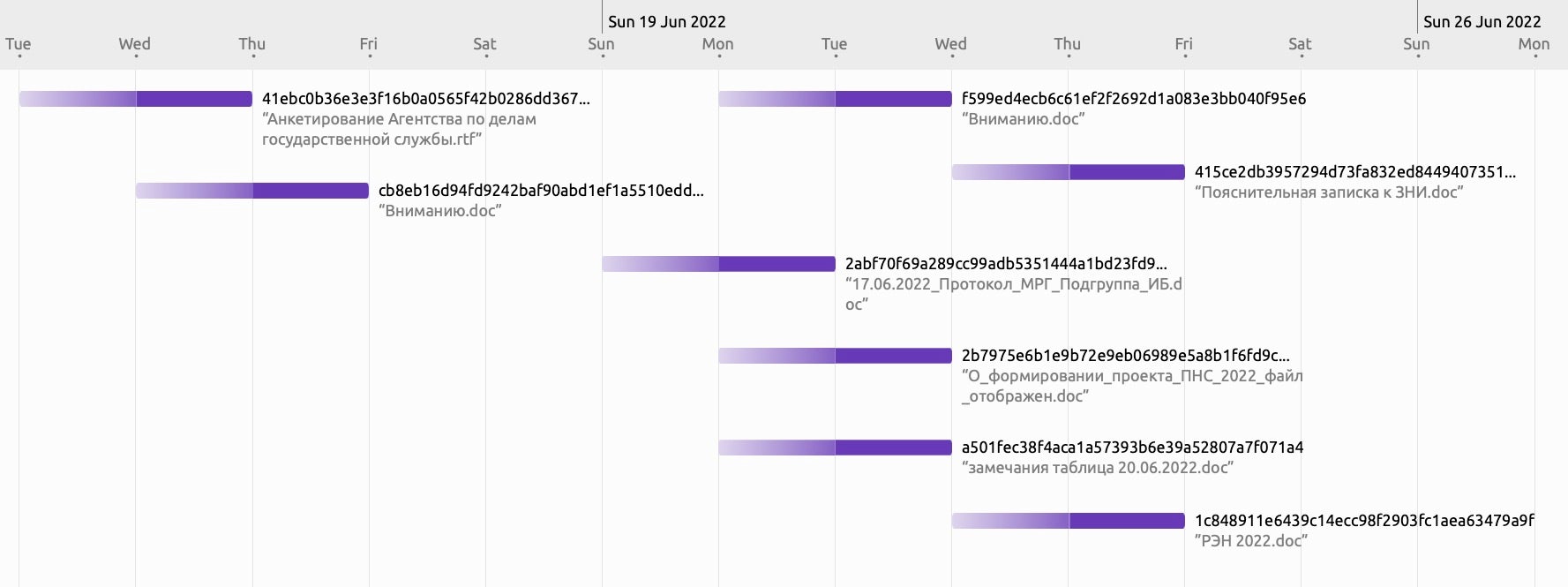
| f599ed4ecb6c61ef2f2692d1a083e3bb040f95e6 | 6/21/2022 Royal Road Document”Вниманию.doc” |
| cb8eb16d94fd9242baf90abd1ef1a5510edd2996 | 6/16/2022 Royal Road Document “Вниманию.doc” |
| 41ebc0b36e3e3f16b0a0565f42b0286dd367a352 | 6/15/2022 (Estimate) Royal Road Document”Анкетирование Агентства по делам государственной службы.rtf” |
| 2abf70f69a289cc99adb5351444a1bd23fd97384 | 6/20/2022 Royal Road Document”17.06.2022_Протокол_МРГ_Подгруппа_ИБ.doc” |
| supportteam.lingrevelat[.]com | C2 Domain |
| upportteam.lingrevelat[.]com | C2 Domain for cb8eb16d94fd9242baf90abd1ef1a5510edd2996 |
| 2b7975e6b1e9b72e9eb06989e5a8b1f6fd9ce027 | 6/21/2022 Royal Road Document”О_формировании_проекта_ПНС_2022_файл_отображен.doc” |
| a501fec38f4aca1a57393b6e39a52807a7f071a4 | 6/21/2022 Royal Road Document”замечания таблица 20.06.2022.doc” |
| 415ce2db3957294d73fa832ed844940735120bae | 6/23/2022 Royal Road Document”Пояснительная записка к ЗНИ.doc” |
| news.wooordhunts[.]com | C2 Domain for 415ce2db3957294d73fa832ed844940735120bae |
| 137.220.176[.]165 | IP Resolved for C2 Domains news.wooordhunts[.]com supportteam.lingrevelat[.]com upportteam.lingrevelat[.]com |
| 1c848911e6439c14ecc98f2903fc1aea63479a9f | 6/23/2022 Royal Road Document”РЭН 2022.doc” |
| 91ca78231bcacab0d5e6194041817b96252e65bf | 5/12/2022 Phishing Email File |
| f444ff2386cd3ada204c3224463f4be310e5554a | 5/12/2022 Royal Road Document”Please help to Check.doc” |
| instructor.giize[.]com | C2 Server for f444ff2386cd3ada204c3224463f4be310e5554a |




