Executive Summary
- A new threat actor SentinelLabs tracks as Agrius was observed operating in Israel starting in 2020.
- Initially engaged in espionage activity, Agrius deployed a set of destructive wiper attacks against Israeli targets, masquerading the activity as ransomware attacks.
- The attacks were carried out using DEADWOOD (aka Detbosit), a wiper with unconfirmed links to an Iranian threat group.
- Agrius actors also dropped a novel wiper named ‘Apostle’ and a custom .NET backdoor called ‘IPsec Helper’.
- Later intrusions carried out by Agrius revealed they kept maintaining and improving Apostle, turning it into a fully functional ransomware.
Agrius Overview
A new threat actor SentinelLabs track as Agrius was observed operating in Israel beginning in 2020. An analysis of what at first sight appeared to be a ransomware attack revealed new variants of wipers that were deployed in a set of destructive attacks against Israeli targets. The operators behind the attacks intentionally masked their activity as ransomware attacks.
One of the wipers used in the attack, dubbed ‘Apostle’, was later turned into a fully functional ransomware, replacing its wiper functionalities. The message inside it suggests it was used to target a critical, nation-owned facility in the United Arab Emirates. The similarity to its wiper version, as well as the nature of the target in the context of regional disputes, leads us to believe that the operators behind it are utilizing ransomware for its disruptive capabilities.
The usage of ransomware as a disruptive tool is usually hard to prove, as it is difficult to determine a threat actor’s intentions. Analysis of the Apostle malware provides a rare insight into such attacks, drawing a clear line between what began as a wiper malware to a fully operational ransomware.
Based on technical analysis of the tools and attack infrastructure, we assess with medium confidence that the attacks were carried out by a threat group affiliated with Iran. While some links to known Iranian actors were observed, the set of TTPs and tools appear to be unique to this set of activities. SentinelLabs tracks this threat actor as Agrius.
Agrius Attack Life Cycle
The Agrius threat group utilizes VPN services (primarily ProtonVPN) for anonymization when accessing the public facing applications of its targets. Upon successful exploitation, the threat actor deploys webshells or simply accesses the target by using the target organization’s VPN solution. The webshells Agrius deploys are mostly variations of ASPXSpy.
Agrius uses those webshells to tunnel RDP traffic in order to leverage compromised accounts to move laterally. During this phase, the attackers use a variety of publicly available offensive security tools for credential harvesting and lateral movement.
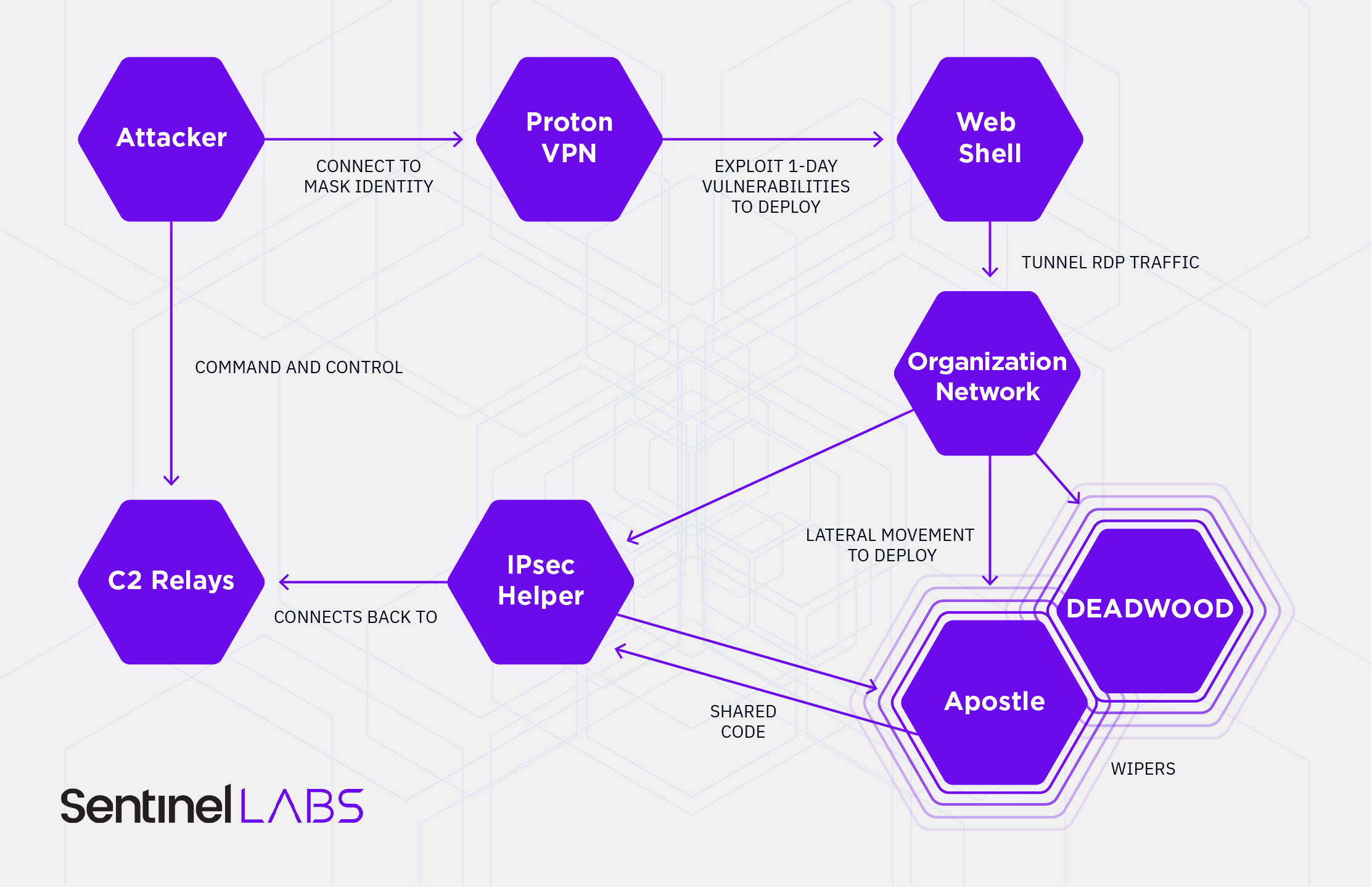
On interesting hosts, the threat actor deploys its own custom malware – ‘IPsec Helper’. This backdoor is written in .NET and appears exclusive to Agrius. The malware registers itself as a service to achieve persistence. It can be used to exfiltrate data or deploy additional malware.
Agrius has deployed two different wipers. The first, dubbed ‘Apostle’, appears to be written by the same developer as ‘IPsec Helper’. Both are written in .NET, share functions, and execute tasks in a similar manner. Interestingly, Apostle was later modified into functioning ransomware. The second wiper, DEADWOOD, was previously involved in a wiping attack in the Middle East and tentatively attributed to Iran.
Attribution
Throughout our analysis of Agrius techniques, tools, and infrastructure, we found no solid links to any known threat groups. While it is hard to provide a definitive attribution for Agrius, a set of indications pointing the activity towards an Iranian nexus came up throughout the investigation:
- Correlation with Iranian interests and past actions
While this is not a strong link, it is worth noting when correlated with other, technical links. Iranian threat actors have a long history of deploying wipers, dating back to 2012, when Iranian hackers deployed the notorious Shamoon malware against Saudi Aramco. Since then, Iranian threat actors have been caught deploying wiper malware in correlation with the regime’s interests on several occasions. - Webshells VirusTotal submissions
Some of the webshells deployed by Agrius throughout its intrusions were modified versions of ASPXSpy, deploying additional obfuscation and changing variable names. Three of the variants of this webshell were uploaded from Iran, the rest from other countries within the Middle East region.
While VirusTotal submissions are not an exact form of determining where a sample was deployed, the sources reinforce a Middle East regional focus.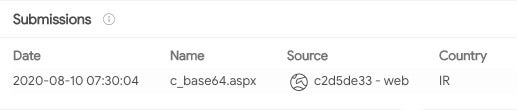
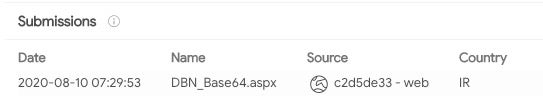
Modified Agrius webshells uploaded from Iran (source: VirusTotal) - Infrastructure links to Iran
The threat actor often used public VPN providers, such as ProtonVPN. On instances where the access was performed from non-VPN nodes, it originated from servers that have also resolved to Iranian domains in the past.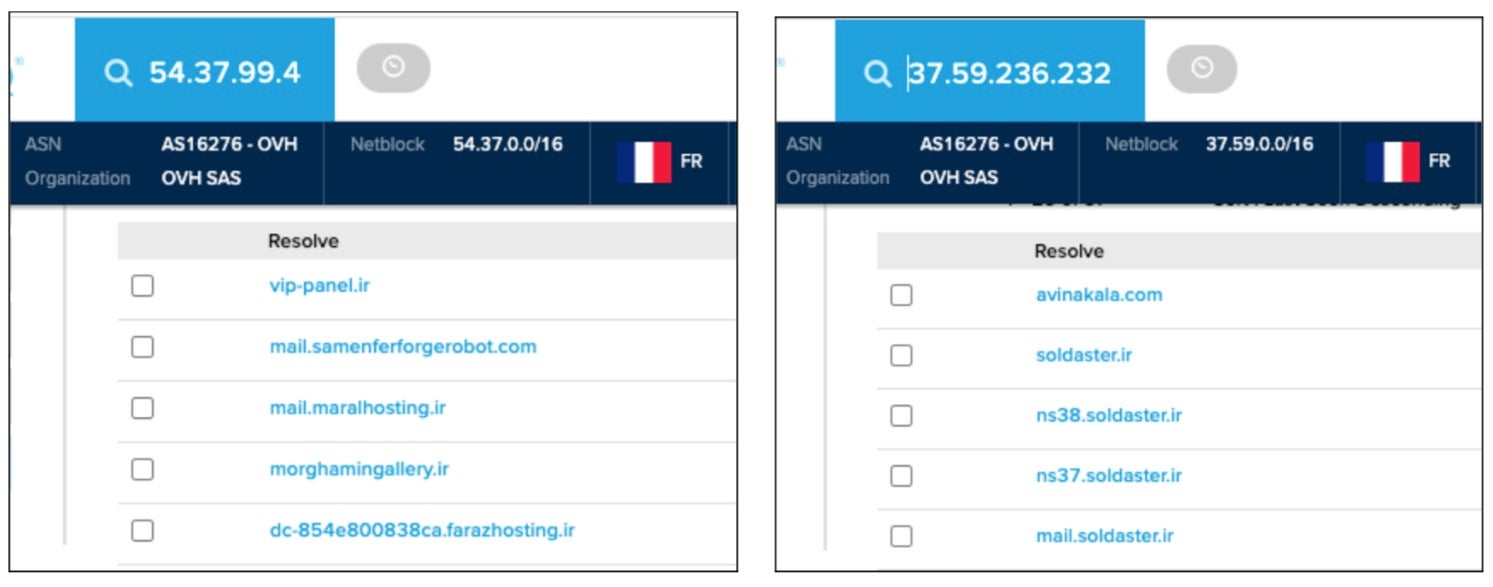
Agrius infrastructure resolving to Iranian domains (source: PassiveTotal) - The usage of the DEADWOOD wiper
Agrius utilized the DEADWOOD wiper, which was previously attributed to an Iranian-nexus actor. We cannot independently corroborate previous clustering claims. The ties between Agrius and the threat actor who originally deployed DEADWOOD remain unclear. It’s possible that the two groups have access to shared resources.
Conclusion
Agrius is a new threat group that we assess with medium confidence to be of Iranian origin, engaged in both espionage and disruptive activity. The group leverages its own custom toolset, as well as publicly available offensive security tools, to target a variety of organizations in the Middle East. In some cases, the group leveraged its access to deploy destructive wiper malware, and in others a custom ransomware. Considering this, we find it unlikely that Agrius is a financially motivated threat actor.
Our analysis of Agrius activity does not come in a vacuum. Early May 2021 saw another set of disruptive ransomware attacks attributed to Iran targeting Israel from the n3tw0rm ransomware group, a newly-identified threat actor with links to the 2020 Pay2Key attacks. The close proximity of the Agrius and n3tw0rm campaigns suggest they may be part of a larger, coordinated Iranian strategy. Leaks from Lab Dookhtegan and the Project Signal ransomware operation also support this claim.
While being disruptive and effective, ransomware activities provide deniability, allowing states to send a message without taking direct blame. Similar strategies have been used with devastating effect by other nation-state sponsored actors. The most prominent of those was NotPetya in 2017, a destructive malware targeting Ukraine masked as ransomware and attributed to Russian state-sponsored threat actors by Western intelligence agencies.
Read the Full Report
See the report for the full list of IOCs and further details on Agrius.




